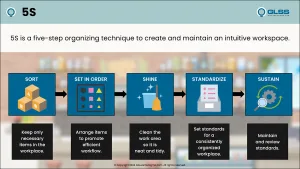
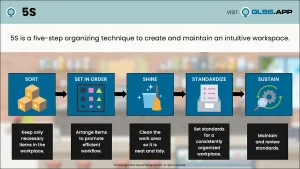
In the Lean community, we all know 5S. It’s workplace organization and a place for everything and everything in its place. It is the foundation of Lean, Visual Controls and where many organizations begin their Lean adventure. However, with the extra emphasis placed on safety in the past 20 years, there has been a tendency to stress the sixth “S”—that of Safety.
Two expressions were born from that emphasis—6S and 5S+1. Some say that 5S+1 was preferred since 6S sounds too much like “success.” In either case, 5S was transformed from its initial SORT, STRAIGHTEN, SHINE, STANDARDIZE and SUSTAIN to add SAFETY.
Adding Security to Workplace Organization
As Lean made its way into the administrative environment in the 2000’s and now further into Hospitals and Healthcare, as well as Customer Service Call Centers, there’s a call for yet another “S.” The seventh “S” stands for Security. Security of patient information, security of credit card or account information. In parallel, in very secure organizations that deal with Department of Defense requirements, military or other secure operations, that seventh “S” was already in place. Security of information, properties, sites, access have all been added to the 6S or 5S+1.
The seventh “S” stands for Security. Security of patient information, security of credit card or account information.
It’s a logical transition, if you think about it. Cybersecurity alone justifies the need to focus on security of passwords, access to applications and more. Nearly every company today has employees that wear ID badges in order to access buildings and work areas. From a Human Resources perspective, confidentiality related to employee counseling, salaries and other sensitive information have driven the need for 7S.

What Does the “S” of Security Look Like?
Let’s look at some detailed examples of the need for Security, the seventh “S.” When it comes to Security, we need to think in terms of personal security and also the security of property, data and access. First, areas should be secure. No open or unlocked doors as appropriate. Employees and visitors should be identified with badges or similar methods. The reception area as well as the docks and yards should all be secured, staffed or monitored to prevent unauthorized access. With the current increase in potential for workplace violence, the need for Security is critical.
For security of data and information, there should be no passwords posted on computers. Computers should automatically lock when not in use to prevent unauthorized access. No sensitive data or confidential information should be on desks, tables or in recycle bins, unless they are locked or currently in use by someone. Sensitive data should not be left on desks or tables after hours. Nor should it be in break rooms, restrooms or other public areas. Some companies have disabled USB drives on their computers to prevent removal of sensitive information or access to their networks for espionage or introduction of malware.
In addition, to have effective security, conversations that may be sensitive or related to confidential information, like employee performance or medical issues, should be held in private or behind closed doors. Conversations in break rooms, restrooms or hallways could be overheard and create security issues. Finally, no sensitive data should be removed from the building or stored with personal belongings without prior approval.
Examples of Success With 7S
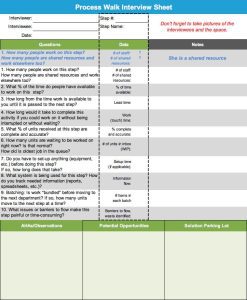
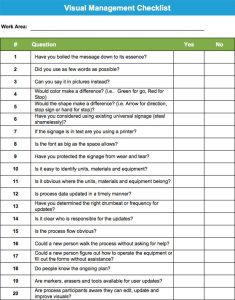
Companies like General Atomics, DJO Global have been using 7S for many years. For General Atomics, the seventh “S” was born from Security as a DOD supplier of unmanned aerial vehicles (UAV) that carry missiles. For DJO Global, the HIPAA act, along with patient and customer credit card information, drove implementation of the seventh “S,” Security, nearly 10 years ago. Below is an audit form used at DJO Global as well as other companies, like the Keefe Supply Company, in their warehouse operations.